
ScamSniffer flags a growing trend in August as crypto scam and fake transaction approvals drain millions from unsuspecting users.
According to security platform ScamSniffer, a trader has lost $3.05 million in a crypto phishing attack. The crypto scam was detected awhile back and was flagged after the user signed a malicious transaction, which gave all access to their wallet to the attackers.
The scammers promptly drained the money, and this shows the growing complexity and speed of Web3 phishing campaigns.
Source : X
This most recent occurrence renews the emphasis on the necessity of transaction validation and wallet security, with several similar exploits having occurred within the first week of August alone.
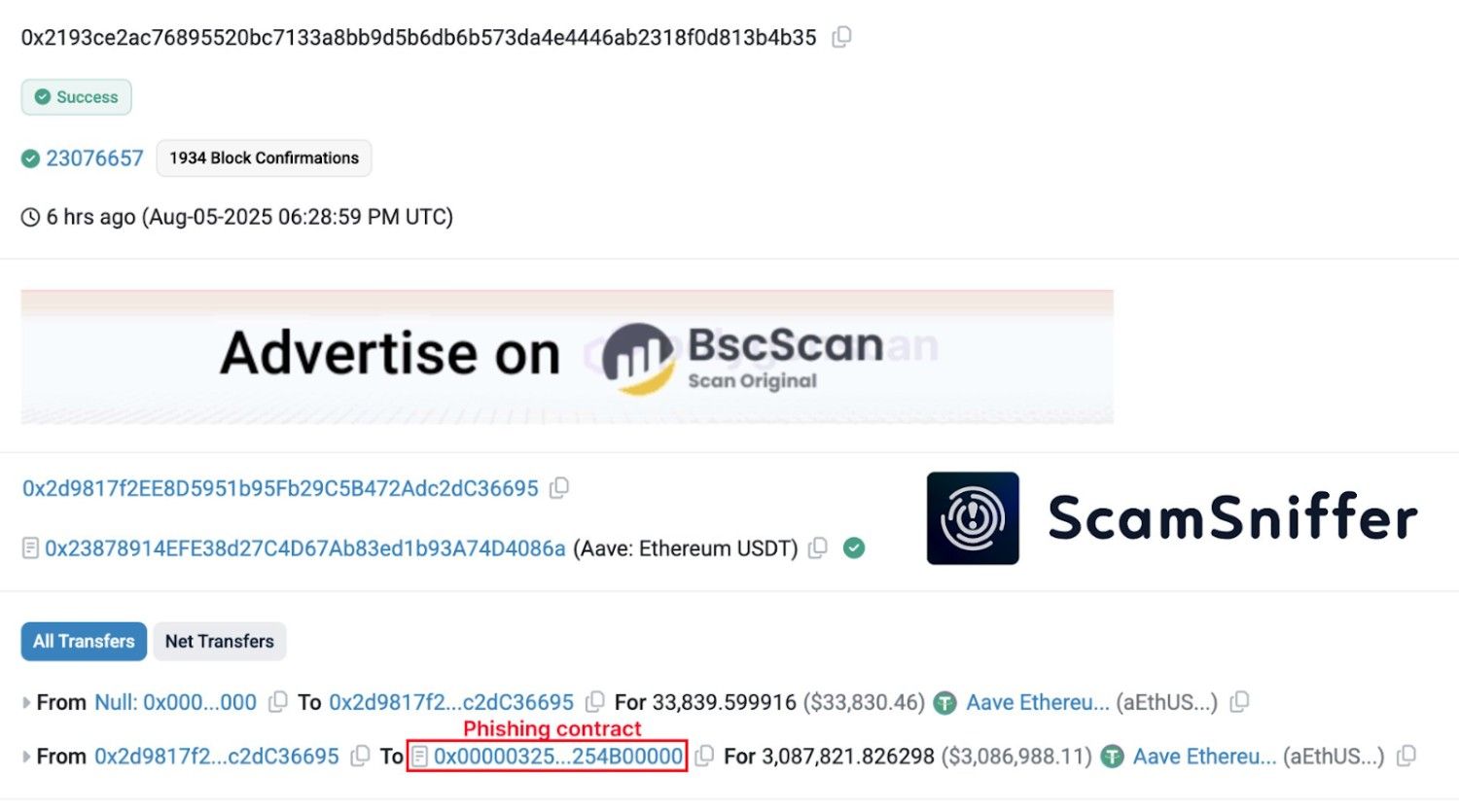
The victim engaged in a contract that did not seem harmful but was flagged as a phishings contract on BscScan. The transaction was detected by ScamSniffer shortly after, and it was verified that the address had already sent more than 3 million USD of Aave Ethereum USDT to a wallet that had been used in the past to conduct malicious activity.
These crypto scam phishing contracts tend to mimic genuine apps or transaction requests, deceiving the user into granting permission to access unlimited tokens. Once signed, the attacker uses these permissions to drain the wallet, often before the victim realizes what happened.
This isn’t an isolated case. ScamSniffer has documented multiple phishing attacks in the first week of August alone:
On August 4, an EIP-7702 upgraded address lost $66,000 in an attack using batch transfers disguised as Uniswap swaps.
Just 18 hours later, another wallet fell victim to the same exploit and lost $33,000.
These followed a May 24 attack where an upgraded address lost $146,551 through a crypto scam.
According to ScamSniffer, the growing number of victims suggests an increase in targeted efforts by scammers, particularly toward EIP-7702 upgraded wallets using newer smart contract features.
Phishing scams in Web3 exploit user trust and interface design. Based on ScamSniffer data, phishing activity is initiated through multiple channels:
Social Media Hacks: Twitter and Discord accounts are hacked, and fake giveaways or emergency messages are posted with malicious links.
Fake Airdrops and Phony Ads: Ads on Google and Twitter are to appear like official token drop or promotions.
Compromised Frontends: In certain instances, DNS or supply chain attacks redirect a user to a mimicked version of a valid site.
Malicious Bots or Expired Invite Links: Commonly used in Discord phishing, bots distribute false links or pose as support teams.
Once a user connects their wallet and approves a transaction, malicious smart contracts exploit permissions like approve, transferFrom, bulkTransfer, or eth_sign, granting access to entire wallets.
ScamSniffer’s threat database lists several commonly abused functions, including:
Tokens: increaseAllowance, approve, withdraw, and permit functions.
NFTs: setApprovalForAll, upgradeTo, and bulkTransfer.
General: eth sign requests and security Update messages from fake apps.
These signatures should serve as red flags for anyone interacting with dApps or new platforms especially when asked to approve actions without clear context.
With these crypto scam attacks, the following best practices are advised by experts:
Always verify the platform URL and never connect to unknown or unverified dApps.
Use tools like ScamSniffer or Revoke.cash to monitor and revoke unnecessary permissions.
Double-check every transaction signature request before clicking “Approve.”
Avoid linking wallets to social media or suspicious Discord invites.
Use hardware wallets for holding large balances; these add an extra layer of security against contract-based phishing.
Another recommendation that ScamSniffer makes is to educate yourself with the help of resources such as unphishable.io and follow the changes in phishing methods within the ecosystem.
This recent $3.05 million crypto scam is a grim reminder of the risks that are still in the crypto field. Whereas blockchain provides transparency and freedom, it also transfers security to the user.
The presence of sophisticated crypto scam, counterfeit dApps, and social engineering has been revealing the vulnerability in Web3 user behavior. Users need to remain vigilant and active since even in August alone, over $4 million in losses in crypto scams have been reported.
As ScamSniffer put it best: “Be cautious of phishing attempts in common scenarios, and familiarize yourself with the types of signatures that can lead to theft.”

Ronny Mugendi is an experienced crypto journalist with four years of professional expertise, having made substantial contributions to multiple media platforms covering cryptocurrency trends and innovations. With more than 4,000 published articles to his name, he is dedicated to informing, educating, and bringing more people into the world of Blockchain and DeFi. Beyond his journalism work, Ronny finds excitement in bike riding, enjoying the adventure of exploring fresh trails and landscapes.