
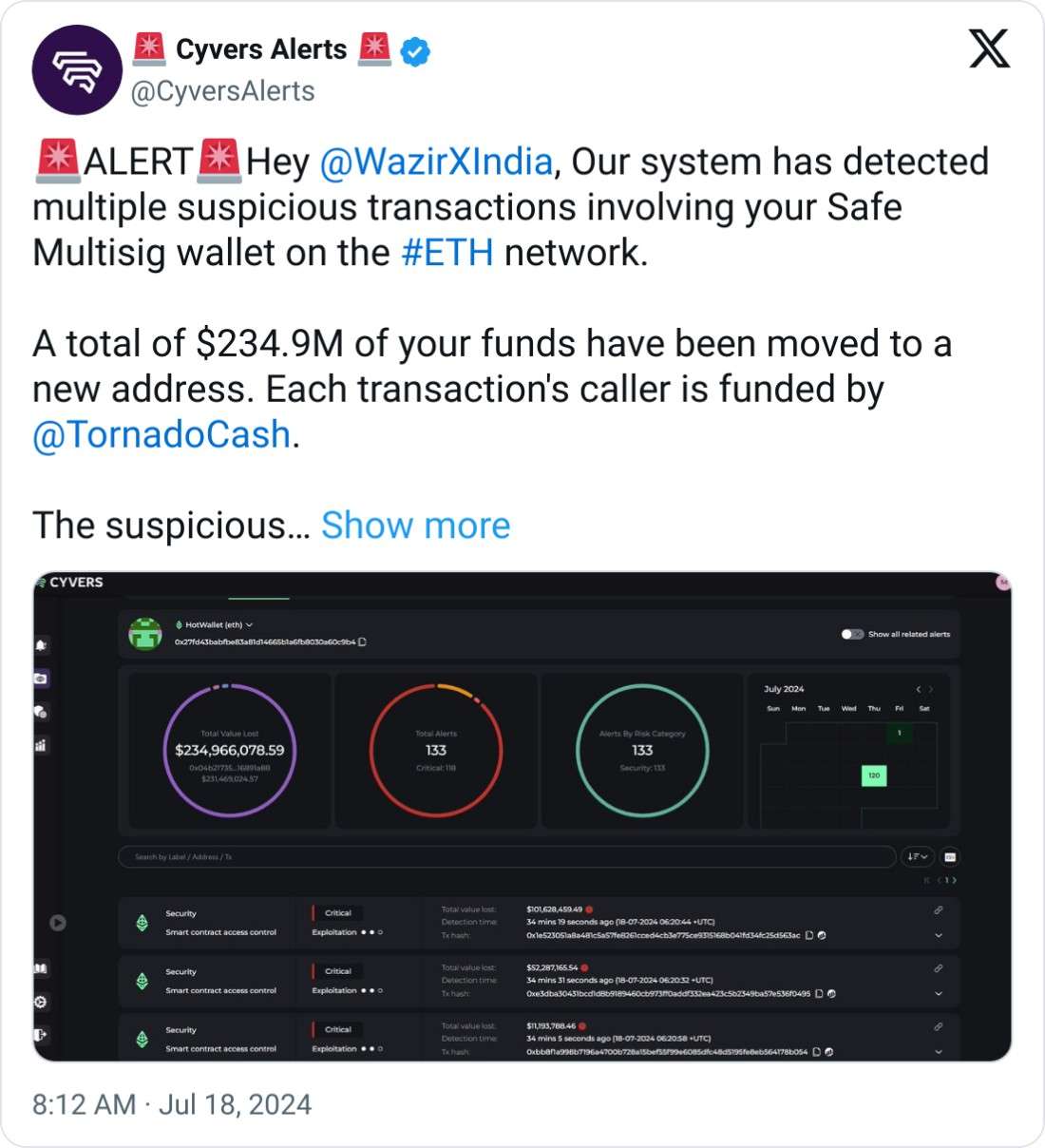
On July 18th, Cyvers Alert, a Web3 security firm, reported something concerning about WazirX, an Ethereum wallet. They found that a large amount of money, $234.9 million, was moved from WazirX's Safe Multisig wallet to a new address. What's worrying is that the transactions were made using Tornado Cash, a tool that hides where money comes from.
After the initial transaction, the funds were converted into Ether, the primary cryptocurrency of Ethereum, and then moved through various other cryptocurrencies such as Tether (USDT), Pepe (PEPE), and Gala (GALA). This process seems to have been designed to obscure the origins and destinations of the funds, making it much more difficult to trace the flow of money across the blockchain.
Cyvers Alert, a well-known Web3 security firm, was responsible for discovering this suspicious activity. Web3, the underlying technology powering cryptocurrencies like Ethereum, has revolutionized digital finance, but incidents like this have sparked widespread debate about the security of these decentralized systems. It has raised questions about how secure blockchain wallets are, particularly multisig wallets—wallets that require multiple approvals before transactions can be completed.
So far, WazirX, the platform that owns the wallet involved, has yet to issue any official statement regarding the incident or provide clarity on how they plan to address it. This lack of transparency has only fueled concerns within the crypto community, making people wonder about the reliability and security of these platforms.
In the ever-evolving world of cryptocurrencies, where transactions are often hard to trace, situations like this emphasize the need for strong security protocols and rigorous compliance standards. As incidents like this continue to surface, there is increasing pressure for the industry to adopt more stringent rules and for platforms to take greater responsibility in safeguarding user funds. The crypto community, along with regulators, will be closely monitoring the situation to see what steps are taken next and how they may shape the future of digital asset protection.
