Highlights
A malicious transaction hit IPOR Fusion Vault Hack on Arbitrum, causing a $336,000 USDC loss.
The exploit affected less than 1% of Fusion’s total funds; other vaults remain safe.
IPOR DAO will fully compensate affected depositors while collaborating with security firms for fund recovery.
On January 6, 2026, the team was alerted to a suspicious transaction on the USDC Fusion Optimizer Vault on Arbitrum. Following a quick research, it was established that the attack had emptied a certain legacy vault of $336,000 USDC. Luckily, the loss is a minor fraction of the total funds of Fusion, and other vaults were not affected.
Security companies like Hexagate and Blockaid were able to cooperate, which helped to detect the incident early, and SEAL is assisting in recovery. The attack demonstrates the fact that even minor misconfigurations of legacy smart contracts can lead to serious vulnerabilities.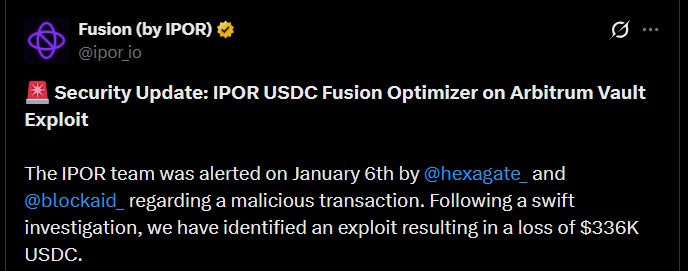
Source: Official X
The breach was due to a flawless storm of susceptibility in the old-fashioned vault:
Vault Logic Error: The impacted vault lacked a validation in its instantWithdraw method. This enabled unauthenticated fuses (logic modules that operated withdrawals) to run arbitrary code.
Admin Account Delegation (EIP-7702): The administrator account was delegating its permissions to a contract that had a function that allowed arbitrary calls. The attacker used this to deceive the Vaults into thinking that the transaction was approved.
Injection of a Malicious Fuse: The attacker used such privileges to inject a malicious fuse. This fuse could withdraw assets because of the missing fuse validation, which transferred 336K USDC to the address of the attacker.
Source: X
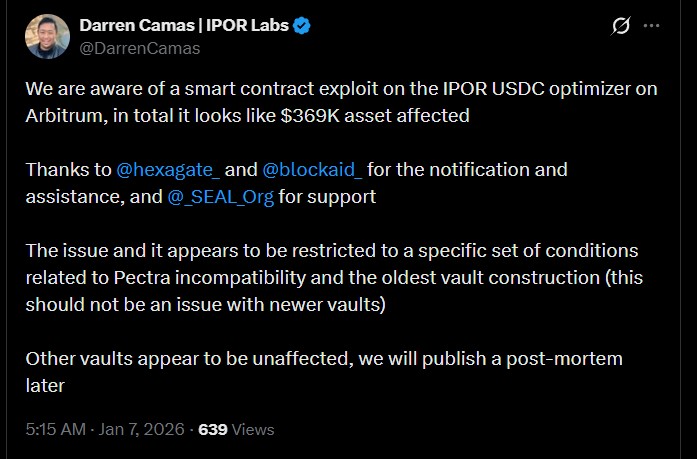
This attack was against a legacy that was deployed approximately 490 days before the implementation of more stringent fuse validation policies. The vulnerable EIP-7702 delegated contract was applied to a small number of older vaults. Newer Fusion Vaults have more validation, and this prevents similar attacks.
In brief, a lack of proper validation and the misuse of delegation provided a special vulnerability, which is impossible to replicate in other vaults.
The team acted fast to guarantee deposit safety:
Recovery Efforts: In conjunction with Hexagate, Blockaid, and SEAL, we are going to monitor and possibly recapture stolen money.
Compensation: The IPOR DAO treasury will bear the loss, with all the depositors that are affected being completely compensated.
Security Assurance: The rest of Fusion Vaults are not impacted and are safe.
IPOR has also undertaken to publish a post-mortem report of the exploit, its causes, and the preventive measures that are being taken.
Although the immediate effects are included, this event is a reminder that the use of legacy smart contracts on Layer-2 networks is associated with certain risks.
In the future, IPOR may probably be stricter in terms of validation, review delegation procedures, and will keep in close collaboration with security companies to eliminate such exploits.
The IPOR Fusion exploit was minor yet instructive in crypto market today: old misconfigurations resulted in a loss of $336K, which was entirely refunded by the DAO, highlighting the ongoing danger of smart contract security.
Disclosure: This is not a financial recommendation. Do your own research prior to investing. CoinGabbar has no liability for any financial losses. Crypto assets have a high level of volatility, and you might lose all your investments.

Sakshi Jain is a crypto journalist with over 3 years of experience in industry research, financial analysis, and content creation. She specializes in producing insightful blogs, in-depth news coverage, and SEO-optimized content. Passionate about bringing clarity and engagement to the fast-changing world of cryptocurrencies, Sakshi focuses on delivering accurate and timely insights. As a crypto journalist at Coin Gabbar, she researches and analyzes market trends, reports on the latest crypto developments and regulations, and crafts high-quality content on emerging blockchain technologies.